Vulnerability Scanning: What It Is And How To Do It Right
While validated scans accumulate better info and also can consequently discover even more susceptabilities than unauthenticated ones, susceptability scanning as a whole generates some false favorable results. That's since there could be susceptabilities that have actually been mitigated with numerous workarounds or safety and security controls without installing patches and also updating the influenced application's variation. Susceptability scanning can trigger network blockage or reduce systems in many cases, which is why they're typically carried out outside routine working hours when they are less most likely to create disruptions.
Safety and security groups can utilize infiltration testing to verify flaws and identify real danger far better without just counting on the extent scores detailed in susceptability databases. Penetration screening also examines the effectiveness of various other defenses that could currently remain in area and might hinder the exploitation of a security issue.
Vulnerability Scanning: What It Is And How To Do It Right
While a network vulnerability scanner checks the web server itself, including its operating system, the internet server daemon as well as the different other open solutions, such as data source solutions working on the exact same system, internet application scanners focus on the code of the application. Unlike network susceptability scanners that use a data source of well-known susceptabilities as well as misconfigurations, internet application scanners seek common sorts of internet problems such as cross-site scripting (XSS), SQL injection, command shot, as well as path traversal.
This is additionally referred to as dynamic application safety screening (DAST) and also is usually utilized by penetration testers. Web application scanners are used with each other with static application safety and security screening (SAST) tools, which analyze the real source code of web applications throughout the advancement stage, as part of safe and secure growth lifecycles (SDLCs).
Vulnerability Scanner Intro And Tips
Relying on exactly how they're set up, outside internet application susceptability scans can generate a whole lot of web traffic, which can overload the web server and also bring about denial-of-service as well as other problems. Due to this, it prevails for vulnerability testing to be integrated right into DevOps and also QA processes by means of supposed interactive application protection testing (IAST) tools that are corresponding to SAST and DAST.
When performed regular monthly or quarterly, susceptability scans just provide a photo in time and do not reflect the security stance of the checked systems in between scans. This can bring about significant blindspots and also is why the safety and security industry suggests raising the regularity of vulnerability scanning as part of a technique called constant vulnerability administration.
Vulnerability Scanner
CIS encourages organizations to release automatic software upgrade devices and also plans in order to guarantee their systems and applications obtain the most up to date safety patches as promptly as possible. Some vendors additionally supply easy scanners or sensing units that continually keep an eye on the network to determine any kind of brand-new systems or applications that are included to the environment.
Several organizations have actually released advice on vulnerability scanning and also monitoring consisting of NIST, US-CERT, the SANS Institute and the UK's NCSC.
Cybersecurity, Simplified: Vulnerability Scanning
All organizations require a way to find susceptabilities on their networks. This is especially real for larger services and those with sensitive databanking, federal government, financing, law, healthcare, and also education are all sectors in which guarding network information as well as framework is vital. But smaller services need to also guarantee their info is safe, without pouring all their IT time and sources right into the job.
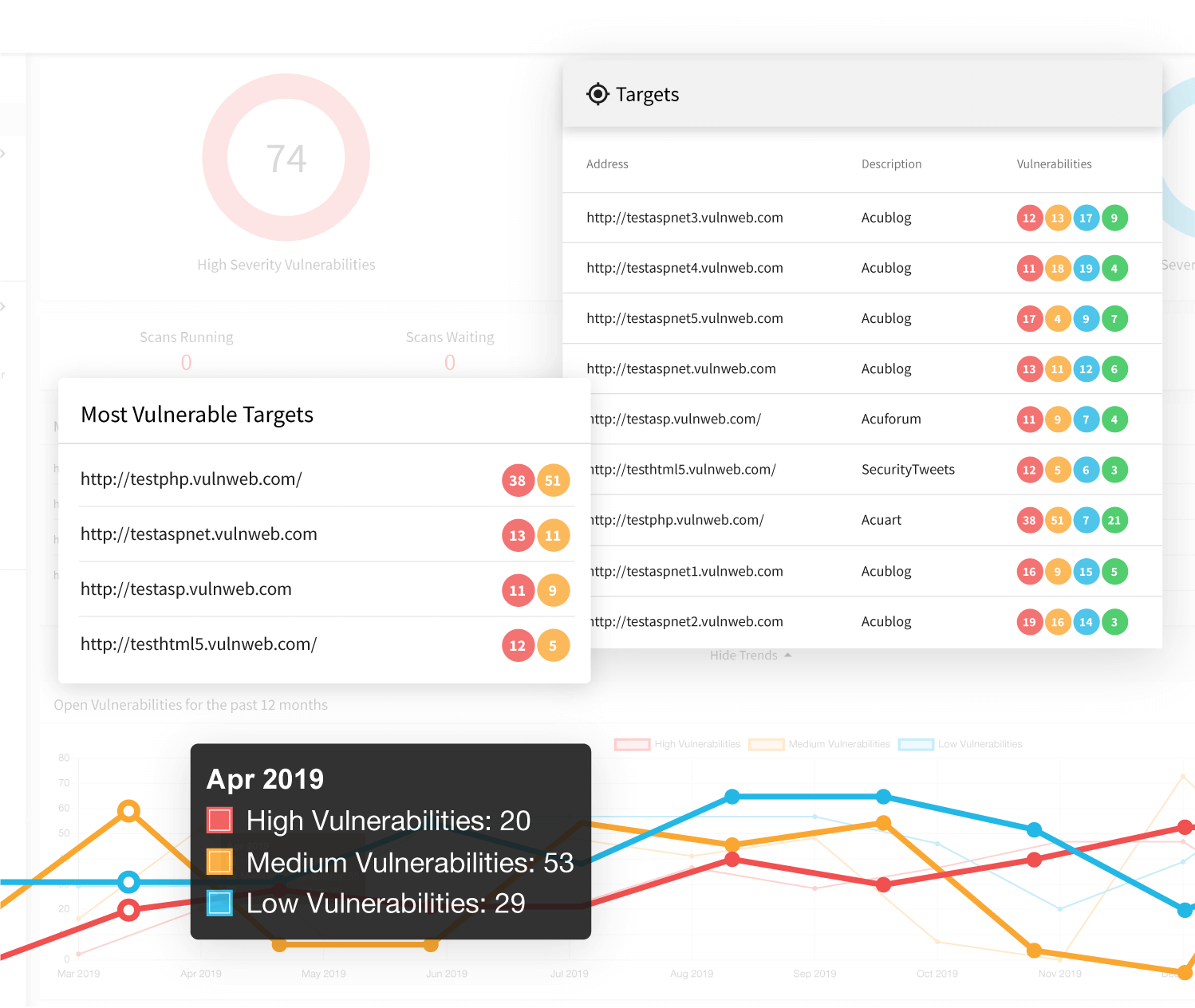
So, what are the most effective susceptability scanners on the market today? In this short article, I assess the top susceptability scanners, both paid as well as complimentary. Network Configuration Manager stands out as my choice for finest general device, as it supplies not only important monitoring understandings but also a method to repair setup concerns promptly across mass devices.
The Importance Of Vulnerability Scans
However you pick to invest your resources, a basic understanding of network vulnerability administration is crucial. This write-up also lays out the basics of vulnerability administration every IT pro needs to understand so you get the most advantages out of your scanning tool. Do you understand if your IT facilities is shielded? Also if end individuals can presently access their documents and also your network connectivity seems great, you can't presume the safety and security of your network.
The goal is to minimize these susceptabilities as long as possible, which is a continuous job, considering your network is continuously used and also transformed while protection threats constantly advance. Susceptability administration has numerous parts. You may believe installing antivirus software program, for example, is sufficient, when as a matter of fact, it has a tendency to leave you playing troubleshooting.
Vulnerability Scanner
Vulnerability scanning devices can make a difference. Basically, susceptability scanning software program can aid IT safety and security admins with the adhering to tasks. Admins require to be able to recognize safety openings in their network, across workstations, servers, firewall programs, and also extra. It takes automated software to capture as a number of these vulnerabilities as Small Business Tech Support possible.
Not all susceptabilities are just as urgent. Scanning devices can categorize and categorize vulnerabilities to aid admins prioritize the most uneasy concerns. As soon as you've determined priority dangers, resolving them can be an overwhelming task. The right device can aid you automate the process of provisioning gadgets. Also after susceptabilities have actually been resolved, it's still vital for admins to show conformity with pertinent regulations.
Network Vulnerability Scanning And Why You Need It Now
There are numerous methods criminals can endanger a network as well as steal information. That said, there prevail safety and security vulnerabilities to look out for. Not every network scanning tool will certainly attend to all these concerns, however you must look for software to help you prioritize some or all of the following hazards.
This susceptability can be protected against with far better network segmentation and monitoring of individual team privileges. Unidentified or unmanaged assets on your network are never ever excellent information. It is necessary to ensure just authorized gadgets have accessibility to your ports. However, experts occasionally abuse their advantages, creating deliberate or unintentional leaks of delicate info, or the misconfiguration of programs, causing additional protection holes.
Vulnerability Scanning Tools
To make sure website application safety, you need to look out for problems like distributed denial-of-service assaults, HTTP misconfigurations, ran out SSL/TLS certificates, and also unconfident code. How you handle your safety setups and framework could open risks. To avoid susceptabilities, look for firewall program or OS misconfigurations. There's a factor no person makes use of Java anymore.